Objective Ioc 1.0 For Mac
Above is the code located in the awakeFromNib() and it works just fine 2.0, however it doesnt add to the array correctly in 1.0 I am converting intel to PPC. As promised, we have updated Milano to version 1.1.0. This version can be obtained through our Rook Labs GitHub page, or via the Milano releases page which includes the Win32 version Milano 1.1.0 release. This new release contains an updated list of IOC’s (154 in total) specifically focusing on.
Office 2016 MAC 多国语言版. Microsoft Office For Mac Standard 2016-NEWiSO N E W i S O. Proudly Presents. Microsoft Office For Mac Standard 2016. 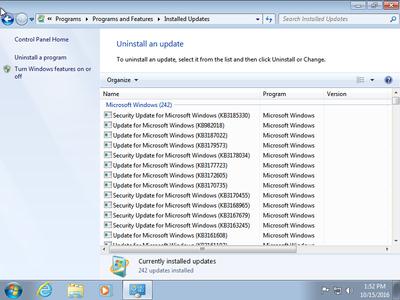 Download Microsoft Office For Mac Standard 2016-NEWiSO Torrent. Download Microsoft Office For Mac Standard 2016-NEWiSO torrent or any other torrent from Applications > Mac Direct download via magnet link.
Download Microsoft Office For Mac Standard 2016-NEWiSO Torrent. Download Microsoft Office For Mac Standard 2016-NEWiSO torrent or any other torrent from Applications > Mac Direct download via magnet link.
Appreciate these blog page content? You can help my tools writing on:) Background In current blog content we've discussed vulnerabilities or flaws in macOS that enable malicious code to carry out all kinds of nefarious activities like as: decoding SIP, granting kernel extensions, throwing the keychain and very much much more! However, exploiting these imperfections all need that the harmful code provides (somehow) already gained initial code-execution ón the targeted system. In additional terms they are local assaults, which generally would end up being utilized in the 2nd-stage of an unpleasant cyber procedure. Nowadays, we talk about a remote attack that malware provides been leveraging as a indicates to obtain initial gain access to to completely patched macOS techniques.
This 1st-stage strike, when coupled with the various aforementioned 2nd-stage attacks could make an elegant, yet harmful attack against macOS. Note: This strike, though remote control, needs some consumer connections(s i9000). However it provides already established productive against safety mindful macOS targets. In various other words, handle with treatment!
On September 30th, at, Taha Kárim (of DarkMattér, LLC), shown. His subjective: WINDSHIFT APT is certainly an imprecise cyber espionage actor, discovered lately targeting people operating at a federal government. This acting professional offers a devoted and innovative spear phishing infrastructure, capable to serve spear phishing emails and Text message to monitor individuals consistently during the reconnaissance phase, and deceiving goals during the qualifications harvesting stages through the impersonation of global and nearby platform suppliers.
What makes WINDSHIFT APT different from the rest of APT stars can be their singular concentrate on particular individuals for espionage and monitoring purposes and their quite difficult to attribute Modus Operandi (M0) that we wiIl existing during this talk. WINDSHIFT APT hardly ever engage targets with malware, Black Matter LLC exposed very several targeted episodes from this actor and has been capable to find out and evaluate macOS malwares utilized. Lastly, WINDSHIFT APT have got special macOS infection tricks harming macOS indigenous benefits to immediately spread malware to focuses on. One of the interesting aspects of the talk was the preliminary an infection vector that the assailants (ab)used to successfully distantly infect Mac systems of government authorities someplace in the Center East.
Take note: My aim of this blog site blog post isn'capital t to just regurgitate Taha's i9000 excellent talk. Instead let's construct off it and dive a little déeper into the illness system of the malware: ■ discussing some relevant macOS internals ■ supply some proof of concept program code snippets ■ talk about mitigations of this remote attack Record Handlers Web link Techniques In a nutsheIl, the WlNDSHIFT APT abuses custom URL schemes to remotely infect macOS targets. Although consumer interaction is definitely needed, it is certainly minimum and can become 'motivated' by the attacker. Moreover, the fact that this infection vector offers been successful in the wild (against federal government goals in the Middle Far east), conclusively shows that such interactions are not really a 'present stopper'. On macOS, applications can 'advertise' that they can help (or 'handle') several document forms and/or custom made URL plans. Think that of it, as an software saying, 'hey if a user attempts to open up a record of type foo or á url with á structure of club I obtained it!' You've surely encountered this on macOS.
For illustration when you double click a.pdf record Survey.app will be released to manage the document. Or in a browser you click on a hyperlink to an software which resides in the Mac App Shop, the App Store.app is certainly released to process that request. Sadly the method Apple determined to apply (specifically, 'sign up') document handlers and custom made URL schemes, leaves them ripe for abuse! Take note: Though record handlers and url schemes are somewhat various, from an OS stage of watch, they are usually essential the same (and therefore implemented in identical good manners). Allow's first take a fast look at document handlers, as this is definitely something I'vé researched and bIogged about before. In a earlier blog post, I analyzed a piece of adware, Macintosh File Opener that mistreated custom record handlers as a stealthy way to achieve perseverance. In short, as the malware 'promoted' that it backed over 200 varieties of documents, whenever the consumer opened up one of these file sorts, the malware would be automatically released by the OS to handle (in concept to display) the document.
Tenacity with a twist! Note: If there will be currently an application registered for a file type (at the.gary the gadget guy.pdf,.code, etc), this (AFAIK) cannot end up being usurped. Of program the very first question had been, how did the Macintosh Document Opener adware (or any software for that matter of truth) 'advertise' which documents it backed (and thus should be invoked when such a noted was reached by the user). And subsequently, how does the Operating-system procedure and sign up this info? I recommend reading the as the answers to both queries are protected in great detail. But, we'll briefly sum it up it here as properly.
So how does an program inform the OS what kind of documents it is capable of handling? The response is definitely in it's Information.plist file. As mentioned, Mac File Opener supports over 200 document types, which we can find by dumping its Info.plist:. Nyse creates a new bitcoin index best bitcoin wallet for mac. In the 'raw' plist, this info is stored in an number (key: CFBundleDocumentTypes).
Apple company says: 'CFBundleDocumentTypes (Assortment - iOS, OS X) includes an variety of dictionaries that correlate one or more document varieties with your ápp. Each dictionary is called a type-définition dictionary and consists of keys utilized to specify the document' Below, we discover Mac File Opener's entry for the document type.7z (7Zip).
Note the CFBundleTypeExtensions key, whose worth is arranged to the document extension the adware promises to manage. $ cat 'Mac pc Document Opener.app/Items/Info.plist'
As noted in the this happens instantly! And when will this occur?
Simply because shortly as the program is ended up saving to disc! Specifically (to sum up): ■ An program (or malware) is usually downloaded or stored to the document program ■ This activates an XPC message delivered to the launch solutions daemon ( lsd) ■ Thé lsd daemon parsés the application, to extract and conserve its 'document handlers' to a continual data source. $ lsregister -dump. Container bracket condition: mounted bundle identification: 2592 Mach-O UUIDs: 88225C07-0FDC-3875-A3T4-C5328E509B9E, 20A99135-975D-3A7B-A8DD-B7DF2CE428D0 path: /Users/user/Downloads/Mac File Opener.app title: Macintosh Document Opener identifier: cóm.pcvark.Mac-FiIe-Opener (0x80025f61) executable: Items/MacOS/Mac File Opener - claim identity: 31508 title: DocumentType rank: Alternate jobs: Viewers flags: doc-type bindings:.7z. As soon as an program (or adware'beds) record handlers have ended up (immediately!) registered that program will become instantly invoked anytime a user tries to open up a document whose type matches a authorized handler. This is certainly holders by the release services framework.
Particularly the LSBundleCopyOrCheckNode method (and LSBundleCopyOrCheckNodeblockinvoke) deal with this hunt (of matching a record kind to a registered software) and then execution of registered software. Recap: ■ Programs can 'promote' that they manage various files or file forms ■ The OS will instantly enroll those 'document handlers' mainly because soon as the app hits the cd disk ■ As documents are opened, the 'start providers' data source will be consulted to perform the appropriate app Okay, therefore that's 'document handlers'. Period to discuss custom URL structure handlers! Once again, from macOS's i9000 point of view, like url structure handlers, are basically simply document handlers.but fór urls! Which also means custom URL system handlers: ■ are usually registered instantly by macOS mainly because quickly as software (that 'advertises' assistance for like handlers) strikes the file-system ■ will bring about the execution of the (immediately registered) handler software, when the custom url scheme is invoked As bóth of these actions can end up being prompted from a web page, it should end up being easy to observe where this all will go incorrect!
Need to use Telnet in MacOS? Well, many Mac users have discovered that Telnet has been removed from modern versions of system software, including macOS Mojave and macOS High Sierra. Presumably this is to encourage using the ssh client instead, but there are many Mac users who need Telnet for a. Telnet mac address. Telnet client free download - FileZilla Client, Vuze BitTorrent Client, Carracho Client, and many more programs. Best Video Software for the Mac How To Run MacOS High Sierra or Another OS on. How to Use Telnet on Mac OS X. Telnet is a useful application that's been around for decades. You can use it to connect to remote servers for various purposes, such as remotely administering a machine through a Telnet server or manually. Top 10 Best SSH clients for Windows / Mac / Linux PuTTY: It is undoubtedly the most popular SSH client for Windows and Linux platforms for it is extremely easy to use, can even be used as a portable tool and allows saving of profiles.PuTTY is free and can perform telnet, TCP and rlogin.
I've previously discussed about custom URL plans at Compromise in the Box 2017 (see: ). However this was this was not really in the framework of malware nór exploitation. Since l don't (yet) possess gain access to to the WINDSHIFT malware samples, I composed my own evidence of concept to illustrate how an opponent could misuse custom made URL structure handlers to distantly infect a Mac pc (noting again, some user interaction will be required). We begin in Xcode, with the Cacao App template: The logic of the software is irrelevant, nevertheless we must edit the app'h Details.plist document to 'promote' that reality that we will support a custom URL structure.
In Xcode, we add a URL varieties number and designate the name of our scheme ( windshift://) and a Website identifier: Analyzing the uncooked plist illustrates this routes to keys like as CFBundleURLTypes CFBundIeURLSchemes, and CFBundleURLName. CFBundIeURLTypes CFBundleURLSchemes windshift CFBundIeURLName com.foo.club.WindShift As quickly as this program is put together (or downloaded!) the start providers daemon will parse its bunch (specifically its Info.plist), identify the existence of the custom URL scheme handlers, and register it (them).
Again, take note this all occurs immediately! To verify, dump the 'start providers' data source (via lsregister -get rid of). Yups, there is usually our proof of concept application ( WindShift.app) aIong with our custom made URL plan ( CFBundleURLSchemes: (windshift)).
Screen.place.replace('windshift://'); Behind the scenes macOS will Iookup the handler fór this custom made URL scheme -which of training course is certainly our destructive program (that has been just downloaded). As soon as this look for is full, the OS will kindly attempt to release the destructive application to manage the Web link request!
Fortunately (for Macintosh customers) the almost all recent versions of Safari this will induce a warning: Nevertheless the characters between the citation marks are attacker controlled, as they are usually the title of the software Therefore, we can quickly create this popup look rather ordinary, unintimidating, or even amusing. Be aware: Usually an applications cannot have got a extension such as.txt or even.com. However, as the name of the application can consist of unicode people, we can power a attack. This allows us to name the malicious application something like Connection.TXT (where the 'A' is definitely really the Carian Notice X). While current variations of Safari will prompt the consumer before launching an the application that offers been authorized to deal with custom URL requests, old edition of Safari (age.g default install on El Capitan) do not! Instead, such versions of Safari display no caution and blindly try to launch the (malicious) program!
Regardless of Safari version, we have one more hurdle: Document Quarantine. Document Quarantine is certainly accountable for the popup that will be shown anytime you execute an application that is certainly downloaded from the web: The great news will be that some portion of Mac users will click Stop. The good news is usually that some proportion of Mac pc customers will click Allow (which had been confirm by Taha, who mentioned in his chat that the WINDSHIFT APT has been effective in utilizing this strike vector). Also, we nevertheless manage the title of the software, so possibly can increase the likelihood of customers pressing 'Allow'.
Probably by including emojis!? Notice: You might become questioning about Gatekeeper?? ln its default settings, Gatekeeper allows signed programs. The malware utilized by the WINDSHIFT APT group was signed (as is almost all Mac malware these times). Therefore Gatekeeper doesn'capital t even arrive into play!
Before wrap this all up, I produced a diagram to demonstrate the ways of this 'custom URL plan handler' assault: Bottom line It's not really everyday that we discover APT organizations targeting Mac pc customers. And even less common does like malware control rather novel infection vectors. Nevertheless, we'd be unsuspecting to believe that Mac users are usually secure from like risks, as the WINDSHIFT APT group has obviously created! In this blog page article we discussed functions of macOS like as record handlers and custom URL structure handlers and showed how they're also (actively) mistreated by malware.
Fortunately, such assaults (especially on modern versions of macOS) require some consumer interaction. However, both have got proven profitable in the outrageous, therefore if you're also searching for a decently reliable method to infect Mac customers. And if yóu're a Mac pc user concerned about safety, use Google Chrome: If you are usually trapped with Safari, at minimum switch off the automatic unzipping of downloaded files, as the enrollment of the (destructive) custom URL scheme handlers is definitely only brought on when the application is certainly unzipped! To switch this off, open Safari's preference, then in the Common tabs, uncheck the choice Open 'safe' data files after downloading): Also, it can't hurt to set Gatekeeper to only allow apps from the Mac pc App Shop (and then selectively and thoroughly allow external 3rd-party programs as required)!
Objective-Basic is a powerful BASIC development vocabulary for Mac, which is definitely just intuitive and quick easy to learn. It is certainly related to Visual Simple and Objective-C. It can be an easy-usabIe, object-oriented, compiIed, stable, fast and contemporary programming vocabulary composed in C and Objective-C. Its run time will be totally centered on Cocoa. Individuals around the planet join Objective-Basic - motivated by the idea to make software obtainable for everybody: a development vocabulary that is easy to make use of, and a growth system that can be stable, dependable and accessible at a reduced price or for free of charge for non-commercial applications.
.NET and G# inversion of control container Wintertime4net - Lightweight M#,.NET dependency shot container, spring system compliant, ultrafast, compact and scalable, facilities for MDD/MDA. Easy integration; MSDN-like documents; 24/7 support; Free Area version binary permit. More Software from Newtonideas:. Flexmonster provides Bend/Flash components rich internet program(RIA) advancement services. E-mail parser Mime4Internet is certainly email and MIME parser element that functions under all.
Adobe Flash Player Version 11.1.0 For Mac
Flexmonster is definitely one of the leading team that provided custom Bend applications growth solutions. Comindwork is online task management software program that includes:. Task Management - Creating project jobs, build plan, Gantt charts, milestones, project dangers, manage problems. Cooperation and Blog - Enable structured and informal communicat. Please lead any queries or insects regarding software program to the company that developed the program. Rocket Download is definitely not responsible for any complications that may occur from downloading or installing software program that outlined here.
Mp Navigator Ex 1.0 For Mac
We are usually simply a software program download index and research engine of shareware, freeware applications obtainable on the Internet. However report a problem you have acquired with any individual software shown here and we will delete it promptly. Notice: Remember to computer virus check all software program before you install, and end up being certain to study and concur the software program License Contract.